
Want to improve your ability to study for the CompTIA CASP+ CAS-004 exam and speed up your pass?
That could not be without the help of the new CAS-004 dumps.
Here’s how: Get help from Pass4itSure, download the new CAS-004 dumps https://www.pass4itsure.com/cas-004.html (updated March 5, 2024) Get new CAS-004 exam questions in PDF, VCE, and Premium Program format as you need to practice.
First, share the most anticipated free exam questions(CAS-004 exam).
Free CompTIA Advanced Security Practitioner (CASP+) CAS-004 dumps exam questions to share online
Provider: Pass4itSure
Number of questions: Last shared CAS-004 Q1-Q13, continuing to share 15 questions/521
Related certifications: CompTIA
Question 1:
A network administrator receives a ticket regarding an error from a remote worker trying to reboot a laptop. The laptop has not yet loaded the operating system, and the user cannot continue the boot process. The administrator can provide the user with a recovery PIN, and the user is able to reboot the system and access the device as needed. Which of the following is the MOST likely cause of the error?
A. Lockout of privileged access account
B. Duration of the BitLocker lockout period
C. Failure of the Kerberos time drift sync
D. Failure of TPM authentication
Correct Answer: D
Question 2:
A security engineer is troubleshooting an issue in which an employee is getting an IP address in the range on the wired network. The engineer plugs another PC into the same port, and that PC gets an IP address in the correct range. The engineer then puts the employee\’ PC on the wireless network and finds the PC still does not get an IP address in the proper range. The PC is up to date on all software and antivirus definitions, and the IP address is not an APIPA address.
Which of the following is MOST likely the problem?
A. The company is using 802.1x for VLAN assignment, and the user or computer is in the wrong group.
B. The DHCP server has a reservation for the PC\’s MAC address for the wired interface.
C. The WiFi network is using WPA2 Enterprise, and the computer certificate has the wrong IP address in the SAN field.
D. The DHCP server is unavailable, so no IP address is being sent back to the PC.
Correct Answer: A
Question 3:
A company has hired a security architect to address several service outages on the endpoints due to new malware. The Chief Executive Officer\’s laptop was impacted while working from home. The goal is to prevent further endpoint disruption. The edge network is protected by a web proxy.
Which of the following solutions should the security architect recommend?
A. Replace the current antivirus with an EDR solution.
B. Remove the web proxy and install a UTM appliance.
C. Implement a deny list feature on the endpoints.
D. Add a firewall module to the current antivirus solution.
Correct Answer: A
Question 4:
Signed applications reduce risks by:
A. encrypting the application\’s data on the device
B. requiring the developer to use code-level hardening techniques.
C. assuring that the application is using unmodified source code.
D. costing the developer money to publish, which reduces the likelihood of malicious intent.
Correct Answer: C
Signing an application primarily ensures the integrity of the application and provides assurance that it hasn’t been tampered with after signing.
Question 5:
Company A has noticed abnormal behavior targeting their SQL server on the network from a rogue IP address. The company uses the following internal IP address ranges: 192.10.1.0/24 for the corporate site and 192.10.2.0/24 for the remote
site. The Telco router interface uses the 192.10.5.0/30 IP range.
Instructions: Click on the simulation button to refer to the Network Diagram for Company A.
Click on Router 1, Router 2, and the Firewall to evaluate and configure each device.
Task 1: Display and examine the logs and status of Router 1, Router 2, and Firewall interfaces.
Task 2: Reconfigure the appropriate devices to prevent the attacks from continuing to target the SQL server and other servers on the corporate network.
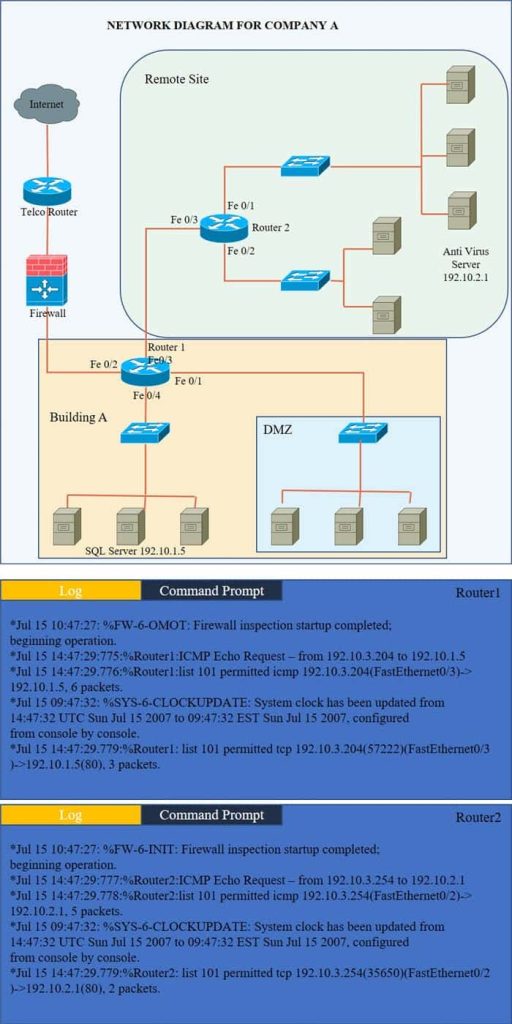
Hot Area:
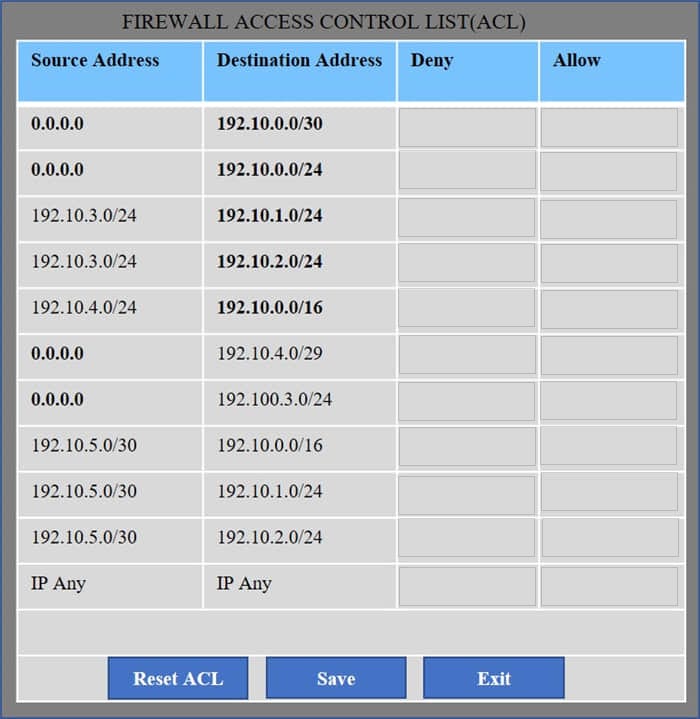
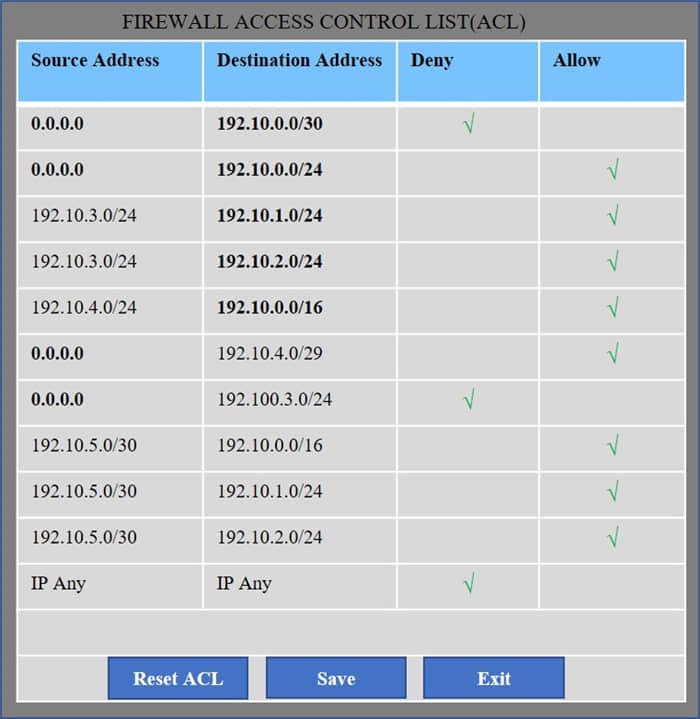
Correct Answer:
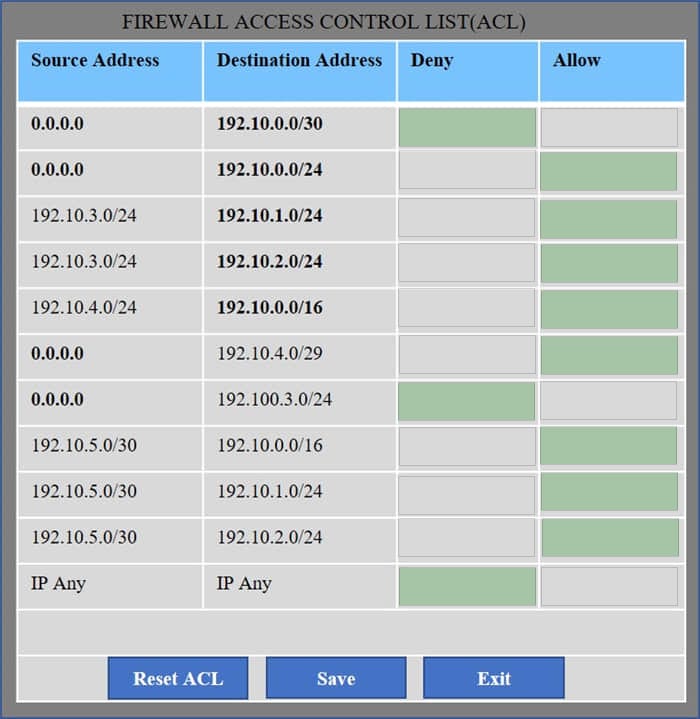
We have traffic coming from two rogue IP addresses: 192.10.3.204 and 192.10.3.254 (both in the 192.10.30.0/24 subnet) going to IPs in the corporate site subnet (192.10.1.0/24) and the remote site subnet (192.10.2.0/24). We need to Deny (block) this traffic at the firewall by ticking the following two checkboxes:
Question 6:
A small business requires a low-cost approach to theft detection for the audio recordings it produces and sells. Which of the following techniques will MOST likely meet the business\’s needs?
A. Performing deep-packet inspection of all digital audio files
B. Adding identifying filesystem metadata to the digital audio files
C. Implementing steganography
D. Purchasing and installing a DRM suite
Correct Answer: C
Question 7:
A customer reports being unable to connect to a website at www.test.com to consume services. The customer notices the web application has the following published cipher suite:
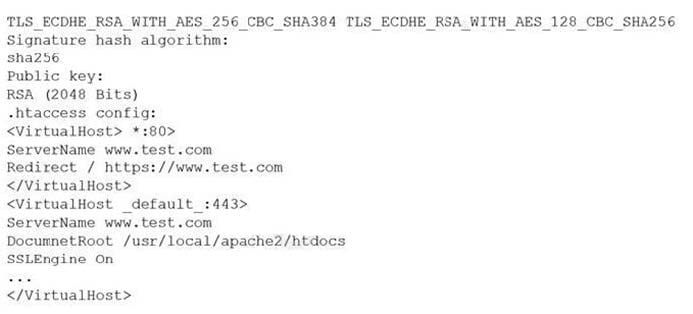
Which of the following is the MOST likely cause of the customer\’s inability to connect?
A. Weak ciphers are being used.
B. The public key should be using ECDSA.
C. The default should be on port 80.
D. The server name should be test.com.
Correct Answer: A
Question 8:
A small company needs to reduce its operating costs. vendors have proposed solutions, which all focus on the management of the company\’s website and services. The Chief Information Security Officer (CISO) insists all available resources in the proposal must be dedicated, but managing a private cloud is not an option. Which of the following is the BEST solution for this company?
A. Community cloud service model
B. Multinency SaaS
C. Single-tenancy SaaS D. On-premises cloud service model
Correct Answer: A
Question 9:
An application server was recently upgraded to prefer TLS 1.3, and now users are unable to connect their clients to the server. Attempts to reproduce the error are confirmed, and clients are reporting the following:
ERR_SSL_VERSION_OR_CIPHER_MISMATCH
Which of the following is MOST likely the root cause?
A. The client application is testing PFS.
B. The client application is configured to use ECDHE.
C. The client application is configured to use RC4.
D. The client application is configured to use AES-256 in GCM.
Correct Answer: C
Reference: https://kinsta.com/knowledgebase/err_ssl_version_or_cipher_mismatch/
Question 10:
A software developer was just informed by the security team that the company\’s product has several vulnerabilities. Most of these vulnerabilities were traced to code the developer did not write. The developer does not recognize some of the code, as it was in the software before the developer started the program and is not tracked for licensing purposes. Which of the following would the developer MOST likely do to mitigate the risks and prevent further issues like these from occurring?
A. Perform supply chain analysis and require third-party suppliers to implement vulnerability management programs.
B. Perform software composition analysis and remediate vulnerabilities found in the software.
C. Perform reverse engineering on the code and rewrite the code more securely.
D. Perform fuzz testing and implement DAST in the code repositories to find vulnerabilities before deployment.
Correct Answer: B
Question 11:
A company in the financial sector receives a substantial number of customer transaction requests via email. While doing a root-cause analysis conceding a security breach, the CIRT correlates an unusual spike in port 80 traffic from the IP address of a desktop used by a customer relations employee who has access to several of the compromised accounts. Subsequent antivirus scans of the device do not return any findings, but the CIRT finds undocumented services running on the device.
Which of the following controls would reduce the discovery time for similar in the future?
A. Implementing application blacklisting
B. Configuring the mall to quarantine incoming attachments automatically
C. Deploying host-based firewalls and shipping the logs to the SIEM
D. Increasing the cadence for antivirus DAT updates to twice daily
Correct Answer: C
Question 12:
A company processes data subject to NDAs with partners that define the processing and storage constraints for the covered data. The agreements currently do not permit moving the covered data to the cloud, and the company would like to renegotiate the terms of the agreements.
Which of the following would MOST likely help the company gain consensus to move the data to the cloud?
A. Designing data protection schemes to mitigate the risk of loss due to multitenancy
B. Implementing redundant stores and services across diverse CSPs for high-availability
C. Emulating OS and hardware architectures to blur operations from the CSP view
D. Purchasing managed FIM services to alert on detected modifications to covered data
Correct Answer: A
Question 13:
A security analyst is investigating a possible buffer overflow attack. The following output was found on a user\’s workstation:
graphic.linux_randomization.org
Which of the following technologies would mitigate the manipulation of memory segments?
A. NX bit
B. ASLR
C. DEP
D. HSM
Correct Answer: B
Reference: http://webpages.eng.wayne.edu/~fy8421/19sp-csc5290/labs/lab2-instruction.pdf (3)
Question 14:
An analyst has prepared several possible solutions to a successful attack on the company. The solutions need to be implemented with the LEAST amount of downtime. Which of the following should the analyst perform?
A. Implement all the solutions at once in a virtual lab and then run the attack simulation. Collect the metrics and then choose the best solution based on the metrics.
B. Implement every solution one at a time in a virtual lab, running a metric collection each time. After the collection, run the attack simulation, roll back each solution, and then implement the next. Choose the best solution based on the best metrics.
C. Implement every solution one at a time in a virtual lab, running an attack simulation each time while collecting metrics. Roll back each solution and then implement the next. Choose the best solution based on the best metrics.
D. Implement all the solutions at once in a virtual lab and then collect the metrics. After collection, run the attack simulation. Choose the best solution based on the best metrics.
Correct Answer: C
Question 15:
Based on PCI DSS v3.4, One Particular database field can store data, but the data must be unreadable. Which of the following data objects meets this requirement?
A. PAN
B. CVV2
C. Cardholder name
D. expiration date
Correct Answer: A
More CompTIA Series Exam Questions…
The most important thing to pass the CompTIA Advanced Security Practitioner (CASP+) exam is to find the right learning resources, I know you.
The following is a list of the latest CAS-004 exam study resources with links.
Latest CAS-004 exam study resources
Book format:
CompTIA Advanced Security Practitioner (CASP+) CAS-004 Cert Guide
Document format:
- Learn online with CertMaster Learn
- Apply your knowledge with CertMaster Labs
- Practice and prepare for your exam with CertMaster Practice
- CompTIA Advanced Security Practitioner
- CompTIA Advanced Security Practitioner (CASP+) 003 vs. 004: What’s the Difference
- COMPTIA CERTMASTER LABS
- CertMaster Labs for CASP+
- CertMaster Learn for CASP+
- CASP+ CAS-004 – 75 CEUs required for certification renewal
If you still have some questions, just ask, this is the place to help you pass the CAS-004 exam.
About CAS-004 exam:
Is it true that to pass the CAS-004 exam, dumps and practice are crucial?
Yes, it’s really important.
Is it possible to pass the CAS-004 exam for a short period of time, such as studying for two days, and then scheduling your CAS-004 exam?
It will be very difficult, and while you may pass the CAS-004 exam, you will not keep anything. This is not recommended.
So there are many good books about the CASP+ CAS-004 exam. Which one of them is the best?
CompTIA CASP+ CAS-004 Certification Guide (Mark Birch)
The last sentence:
With the help of using the new CAS-004 dumps can improve your learning and pass the ability to take the exam, which is recognized by practice.
Go and download now the new CAS-004 dumps https://www.pass4itsure.com/cas-004.html (PDF, VCE, Premium Program) to get the new CAS-004 exam questions to practice. Coupled with careful study of exam resources, I believe that success in the exam must belong to you.



