Without the preparation of CompTIA PT0-001 dumps learning materials, no goals can be achieved. Fortunately, you can take advantage of the available CompTIA PenTest + PT0-001 books, help guides, video training, Eminent https://www.pass4itsure.com/pt0-001.html CompTIA PT0-001 dumps the most effective…
Getting Insight into PT0-001 Exam:
which focuses on the following technology:
- CompTIA PenTest+
- Skills and Expertise required for CompTIA PenTest+ (Plus) Exam: https://www.comptia.org/certifications/pentest
Preparation Essential for CompTIA PenTest+ PT0-001 Exam:
Pass4itsure.com is well known for providing best and reliable study material for PT0-001 exam preparation.

CompTIA PT0-001 Dumps PDF 2020
[drive] CompTIA PT0-001 Dumps PDF Free https://drive.google.com/file/d/1lgBPhRttiICJvq-c88LXkNUSG1nKdA2w/view?usp=sharing
PT 0-001 exam dumps: PT 0-001 questions and answers
CompTIA PenTest+ PT0-001 practice test
QUESTION 1
Joe, a penetration tester, is asked to assess a company\\’s physical security by gaining access to its corporate office.
Joe ism looking for a method that will enable him to enter the building during business hours or when there are no
employee on-site. Which of the following would be MOST effective in accomplishing this?
A. Badge cloning
B. Lock picking
C. Tailgating
D. Piggybacking
Correct Answer: A
http://www.hackingarticles.in/netbios-and-smb-penetration-testing-on- windows/
QUESTION 2
A penetration tester identifies the following findings during an external vulnerability scan:
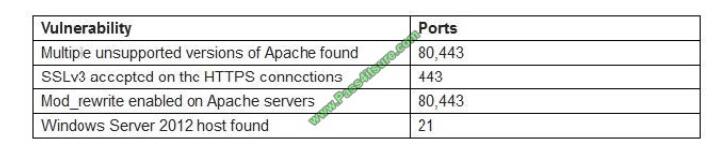
Which of the following attack strategies should be prioritized from the scan results above?
A. Obsolete software may contain exploitable components
B. Weak password management practices may be employed
C. Cryptographically weak protocols may be intercepted
D. Web server configurations may reveal sensitive information
Correct Answer: C
QUESTION 3
Joe, an attacker, intends to transfer funds discreetly from a victim\\’s account to his own. Which of the following URLs
can he use to accomplish this attack?
A. https://testbank.com/BankingApp/ACH.aspx?CustID=435345andaccountType=FandactionACHTransferandsenderID=654846andnotify=Falseandcreditaccount=\\’OR 1=1 AND select username from testbank.custinfo where username like `Joe\\’andamount=200
B. https://testbank.com/BankingApp/ACH.aspx?CustID=435345andaccountType=FandactionACHTransferandsenderID=654846andnotify=Falseandcreditaccount=\\’OR 1=1 AND select username from
testbank.custinfo where username like `Joe\\’ andamount=200
C. https://testbank.com/BankingApp/ACH.aspx?CustID=435345andaccountType=FandactionACHTransferandsenderID=654846andnotify=Trueandcreditaccount=\\’OR 1=1 AND select username from
testbank.custinfo where username like `Joe\\’ andamount=200
D. https://testbank.com/BankingApp/ACH.aspx?CustID=435345andaccountType=FandactionACHTransferandsenderID=654846andnotify=Trueandcreditaccount=\\’AND 1=1 AND select username from
testbank.custinfo where username like `Joe\\’ andamount=200
Correct Answer: B
QUESTION 4
An attacker uses SET to make a copy of a company\\’s cloud-hosted web mail portal and sends an email m to obtain the
CEO s login credentials Which of the following types of attacks is this an example of?
A. Elicitation attack
B. Impersonation attack
C. Spear phishing attack
D. Drive-by download attack
Correct Answer: C
QUESTION 5
A security analyst was provided with a detailed penetration report, which was performed against the organization\\’s
DMZ environment. It was noted on the report that a finding has a CVSS base score of 10.0. Which of the following
levels of difficulty would be required to exploit this vulnerability?
A. Very difficult; perimeter systems are usually behind a firewall.
B. Somewhat difficult; would require significant processing power to exploit.
C. Trivial; little effort is required to exploit this finding.
D. Impossible; external hosts are hardened to protect against attacks.
Correct Answer: C
Reference https://nvd.nist.gov/vuln-metrics/cvss
QUESTION 6
The following command is run on a Linux file system:
Chmod 4111 /usr/bin/sudo
Which of the following issues may be exploited now?
A. Kernel vulnerabilities
B. Sticky bits
C. Unquoted service path
D. Misconfigured sudo
Correct Answer: B
QUESTION 7
A penetration tester locates a few unquoted service paths during an engagement. Which of the following can the tester
attempt to do with these?
A. Attempt to crack the service account passwords.
B. Attempt DLL hijacking attacks.
C. Attempt to locate weak file and folder permissions.
D. Attempt privilege escalation attacks.
Correct Answer: D
QUESTION 8
Place each of the following passwords in order of complexity from least complex (1) to most complex (4), based on the
character sets represented Each password may be used only once.
Select and Place:
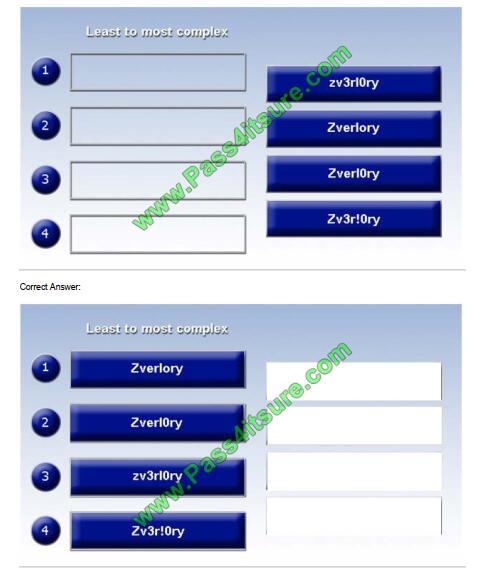
QUESTION 9
A company planned for and secured the budget to hire a consultant to perform a web application penetration test. Upon
discovered vulnerabilities, the company asked the consultant to perform the following tasks:
Code review Updates to firewall setting
A. Scope creep
B. Post-mortem review
C. Risk acceptance
D. Threat prevention
Correct Answer: D
QUESTION 10
A manager calls upon a tester to assist with diagnosing an issue within the following:
Python script: #!/usr/bin/python s = “Administrator” The tester suspects it is an issue with string slicing and manipulation
Analyze the following code segment and drag and drop the correct output for each string manipulation to its
corresponding code segment Options may be used once or not at all.
Select and Place:

Correct Answer:

QUESTION 11
Given the following script:
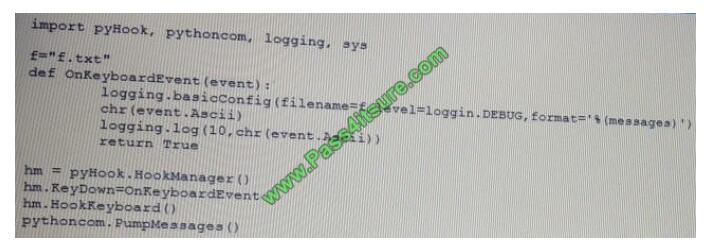
Which of the following BEST describes the purpose of this script?
A. Log collection
B. Event logging
C. Keystroke monitoring
D. Debug message collection
Correct Answer: C
QUESTION 12
A penetration tester is performing a black box assessment on a web-based banking application. The tester was only
provided with a URL to the login page. Give the below code and output
Import requests
from BeautifulSoup import BeautifulSoup
request = requests.get (“https://www.bank.com/admin”)
respHeaders, respBody = request[0]. Request[1]
if respHeader.statuscode == 200:
soup = BeautifulSoup (respBody)
soup = soup.FindAll (“div”, (“type” : “hidden”))
print respHeader. StatusCode, StatusMessage
else:
print respHeader. StatusCode, StatusMessage
Output: 200 OK
Which of the following is the tester intending to do?
A. Horizontally escalate privileges
B. Scrape the page for hidden fields
C. Analyze HTTP respond code
D. Search for HTTP headers
Correct Answer: B
QUESTION 13
If a security consultant comes across a password hash that resembles the following b117 525b3454
7Oc29ca3dBaeOb556ba8 Which of the following formats is the correct hash type?
A. Kerberos
B. NetNTLMvl
C. NTLM
D. SHA-1
Correct Answer: D
The latest CompTIA Server+ SK0-004 exam Practice Questions and Answers
Latest reviews of Pass4itsure
Latest discount code “2020PASS” – Pass4itsure
Please read the picture carefully to get 12% off!

PS.
Just follow https://www.pass4itsure.com/pt0-001.html PT0-001 dumps which is based on real PT0-001 questions and pass the exam in the first attempt.
2020 Pass4itsure PT0-001 Dumps PDF Free Share(Q1-Q13)
https://drive.google.com/file/d/1rnx8enaNWU1JZgIXdwG86OduS5MFkqEf/view?usp=sharing


