Do you need Guaranteed Pass4itsure Q&A for the 70-483 dumps exam? The Programming in C# (70-483 Visual Studio) exam is a 242-question assessment in pass4itsure that is associated with the MCP, and MCSA certification.
Latest Microsoft 70-483 dumps Visual Studio exam questions actual 70-483 dumps Youtube training will be more popular. “Programming in C#” is the exam name of the Pass4itsure Microsoft 70-483 dumps test which is designed to help candidates prepare for and pass the Microsoft 070-483 exam. Microsoft https://www.pass4itsure.com/70-483.html dumps exam certification with the highest standards of professional and technical information, as the knowledge of experts and scholars to study and research purposes.
All of the products we provide have a part of the free trial before you buy to ensure that you fit with this set of data.
[New Microsoft 70-483 Dumps Release From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWQUM2eV9yZ2hMNTQ
[New Microsoft 070-464 Dumps Release From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWY000Mkw0VEZqYWM
Pass4itsure Microsoft 70-483 Dumps Training Program Online Here:
QUESTION 18:
You are creating a class named Employee. The class exposes a string property named EmployeeType. The following code segment defines the Employee class. (Line numbers are included for reference only.)
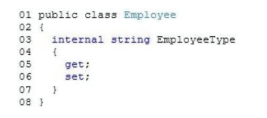
The EmployeeType property value must be accessed and modified only by code within the Employee class or a class derived from the Employee class. You need to ensure that the implementation of the EmployeeType property meets the requirements.
Which two actions should you perform? (Each correct answer represents part of the complete solution. Choose two.)
A. Replace line 05 with the following code segment: protected get;
B. Replace line 06 with the following code segment: private set;
C. Replace line 03 with the following code segment: public string EmployeeType
D. Replace line 05 with the following code segment: private get;
E. Replace line 03 with the following code segment: protected string EmployeeType
F. Replace line 06 with the following code segment: protected set;
Correct Answer: BE
Explanation
Explanation/Reference:
QUESTION 19:
You are implementing a method named Calculate that performs conversions between value types and reference types. The following code segment implements the method. (Line numbers are included for reference only.)
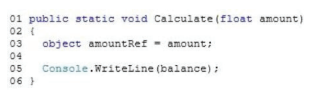
You need to ensure that the application does not throw exceptions on invalid conversions. Which code segment should you insert at line 04?
A. int balance = (int) (float)amountRef;
B. int balance = (int)amountRef;
C. int balance = amountRef;
D. int balance = (int) (double) amountRef;
Correct Answer: A
Explanation
Explanation/Reference:
QUESTION 20:
You are creating a console application by using C#. You need to access the application assembly. Which code segment should you use?
A. Assembly.GetAssembly(this);
B. this.GetType();
C. Assembly.Load();
D. Assembly.GetExecutingAssembly();
Correct Answer: D
Explanation
Explanation/Reference:
Explanation:
QUESTION 21:
HOTSPOT
You are implementing a library method that accepts a character parameter and returns a string. If the lookup succeeds, the method must return the corresponding string value. If the lookup fails, the method must return the value “invalid choice.” You need to implement the lookup algorithm. How should you complete the relevant code? (To answer, select the correct keyword in each drop-down list in the answer area.)
Hot Area:
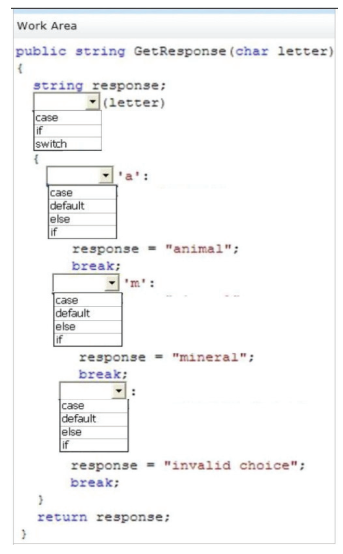
Correct Answer:
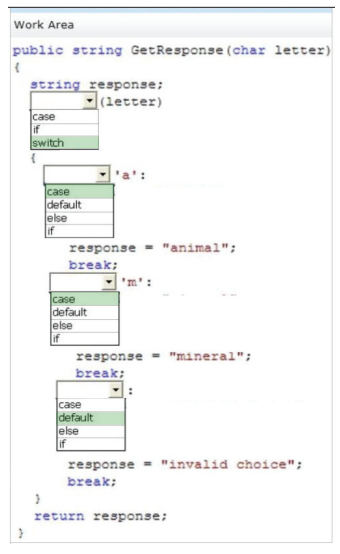
Explanation
Explanation/Reference:
Explanation:
QUESTION 22:
You use the Task.Run() method to launch a long-running data processing operation. The data processing operation often fails in times of heavy network congestion.
If the data processing operation fails, a second operation must clean up any results of the first operation. You need to ensure that the second operation is invoked only if the data processing operation throws an unhandled exception.
What should you do?
A. Create a TaskCompletionSource<T> object and call the TrySetException() method of the object.
B. Create a task by calling the Task.ContinueWith() method.
C. Examine the Task.Status property immediately after the call to the Task.Run() method.
D. Create a task inside the existing Task.Run() method by using the AttachedToParent option.
Correct Answer: B
Explanation
Explanation/Reference:
QUESTION 23:
You are modifying an application that processes leases. The following code defines the Lease class. (Line numbers are included for reference only.) 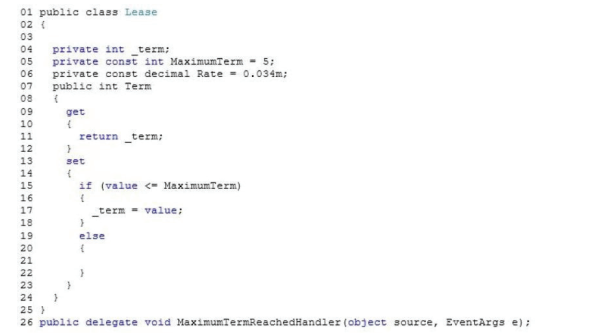
Leases are restricted to a maximum term of 5 years. The application must send a notification message if a lease request exceeds 5 years. You need to implement the notification mechanism. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
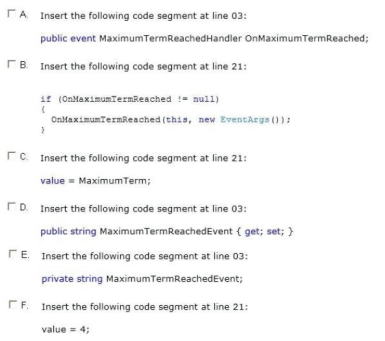
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
F. Option F
Correct Answer: AB
Explanation
Explanation/Reference:
QUESTION 24:
What is the benefit of cloud computing over traditional computing?
A. Reduces the time to provision and deploy new applications
B. Eliminates consumer’s IT operational expenditure
C. Enables the use of proprietary APIs to access IT resources
D. Lowers migration cost and prevents vendor lock-in
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
Benefits of Cloud Computing
Cloud computing offers the following key benefits: Reduced IT cost: Cloud services can be purchased based on pay-per-use or subscription pricing. This reduces or eliminates consumer’s IT capital expenditure (CAPEX).
Business agility:
Cloud computing provides the capability to allocate and scale computing capacity quickly. Cloud can reduce the time required to provision and deploy new applications and services from months to minutes. This enables businesses to respond more quickly to market changes and reduce time-to-market. Flexible scaling: Cloud computing enables consumers to scale up, scale down, scale out, or scale in the demand for computing resources easily.
Consumers can unilaterally and automatically scale computing resources without any interaction with cloud service providers. The flexible service provisioning capability of the cloud often provides a sense of unlimited scalability to the cloud service consumers.
High availability: Cloud computing can ensure resource availability at varying levels depending on the consumer’s policy and priority. Redundant infrastructure components (servers, network paths, and storage equipment, along with clustered software) enable fault tolerance for cloud deployments. These techniques can encompass multiple data centers located in different geographic regions, which prevents data unavailability due to regional failures. EMC E10-001 Student Resource Guide.
Module 13: Cloud Computing
QUESTION 25:
Which statement describes a denial of service attack?
A. Prevents authorized users from accessing the resources and services
B. Prohibits attempts to repair the resources and services after an attack
C. Attempts to provide false information by impersonating someone’s identity
D. Prevents unauthorized users to access the resources and services
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
Threats are the potential attacks that can be carried out on an IT infrastructure. These attacks can be classified as active or passive.
Passive attacks are attempts to gain unauthorized access to the system. They pose threats to the confidentiality of information. Active attacks include data modification, denial of service (DoS), and repudiation attacks. They pose threats to data integrity, availability, and accountability.
In a data modification attack, the unauthorized user attempts to modify information for malicious purposes.
A modification attack can target the data at rest or the data in transit. These attacks pose a threat to data integrity. Denial of service (DoS) attacks prevent legitimate users from accessing resources and services. These attacks generally do not involve access to or modification of information. Instead, they pose a threat to data availability.
The intentional flooding of a network or website to prevent
legitimate access to authorized users is one example of a DoS attack. Repudiation is an attack against the accountability of information. It attempts to provide false information by either impersonating someone’s identity or denying that an event or a transaction has taken place.
For example, a repudiation attack may involve performing an action and eliminating any evidence that could prove the identity of the user (attacker) who performed that action. Repudiation attacks include circumventing the logging of security events or tampering with the security log to conceal the identity of the attacker.
QUESTION 26:
What is a key benefit of virtualization?
A. Improved resource utilization
B. Improved performance
C. Enhanced interoperability
D. Unlimited resource scaling
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
QUESTION 27:
What is an accurate statement about the Data Center Bridging Exchange protocol?
A. Enables Converged Enhanced Ethernet (CEE) devices to convey and configure their features with other CEE devices
B. Creates virtual FCoE links over an existing Ethernet network to transport FC frames over virtual links independently
C. Enables an FCoE switch to send signals to other FCoE switches that need to stop or slow down their transmissions
D. Enables an FCoE switch to transport both TCP/IP and FC frames over a single virtual FCoE link
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
Data Center Brdiging Exchange Protocol (DCBX)
DCBX protocol is a discovery and capability exchange protocol, which helps Converged Enhanced Ethernet devices to convey and configure their features with the other CEE devices in the network. DCBX is used to negotiate capabilities between the switches and the adapters, and it allows the switch to distribute the configuration values to all the attached adapters. This helps to ensure consistent configuration across the entire network.
QUESTION 28:
What is a key security consideration when a NAS device enables the sharing of the same data among UNIX and Microsoft Windows users?
A. NAS device must map UNIX permissions to Windows and vice versa
B. NAS defines and maintains ownership of the objects
C. NIS server must separately maintain SIDs for UNIX and Windows environments
D. Object permissions are not defined in advance and assigned dynamically
Correct Answer: A
Explanation
Explanation/Reference:
Explanation:
Authorization defines user privileges in a network.
The authorization techniques for UNIX users and Windows users are quite different. UNIX files use mode bits to define access rights granted to owners, groups, and other users, whereas Windows uses an ACL to allow or deny specific rights to a particular user for a particular file.
Although NAS devices support both of these methodologies for UNIX and Windows users, complexities arise when UNIX and Windows users access and share the same data. If the NAS device supports multiple protocols, the integrity of both permission methodologies must be maintained.
NAS device vendors provide a method of mapping UNIX permissions to Windows and vice versa, so a multiprotocol environment can be supported.
QUESTION 29:
An attacker finds a web page for a target organization that supplies contact information for the company. Using available details to make the message seem authentic, the attacker drafts an e-mail to an employee on the contact page that appears to come from an individual who might reasonably request confidential information, such as a network administrator.
The email asks the employee to log into a bogus page that requests the employee’s user name and password or click on a link that will download spyware or other malicious programming.
Google’s Gmail was hacked using this technique and attackers stole source code and sensitive data from Google servers.
This is a highly sophisticated attack using zero-day exploit vectors, social engineering, and malware websites that focus on targeted individuals working for the company.
What is this deadly attack called?
A. Spear phishing attack
B. Trojan server attack
C. Javelin attack
D. Social networking attack
Answer: A
QUESTION 30:
Vulnerability scanners are automated tools that are used to identify vulnerabilities and misconfigurations of hosts. They also provide information regarding mitigating discovered vulnerabilities.
Which of the following statements is incorrect?
A. Vulnerability scanners attempt to identify vulnerabilities in the hosts scanned.
B. Vulnerability scanners can help identify out-of-date software versions, missing patches, or system upgrades
C. They can validate compliance with or deviations from the organization’s security policy
D. Vulnerability scanners can identify weaknesses and automatically fix and patch the vulnerabilities without user intervention
Answer: D
QUESTION 31:
How does traceroute map the route a packet travels from point A to point B?
A. Uses a TCP timestamp packet that will elicit a time exceeded in transit message
B. Manipulates the value of the time to live (TTL) within the packet to elicit a time exceeded in transit message
C. Uses a protocol that will be rejected by gateways on its way to the destination
D. Manipulates the flags within packets to force gateways into generating error messages
Answer: B
QUESTION 32:
How do you defend against the DHCP Starvation attack?
A. Enable ARP-Block on the switch
B. Enable DHCP snooping on the switch
C. Configure DHCP-BLOCK to 1 on the switch
D. Install DHCP filters on the switch to block this attack
Answer: B
QUESTION 33:
What type of session hijacking attack is shown in the exhibit?
A. Cross-site scripting Attack
B. SQL Injection Attack
C. Token sniffing Attack
D. Session Fixation Attack
Answer: D
…
Summarize:
If you want to buy Microsoft 070-483 dumps exam information, Pass4itsure will provide the best service and the best quality products. “Programming in C#”, also known as the 070-483 exam, is a Microsoft certification that covers all the knowledge points of the real Microsoft exam.
Pass4itsure Microsoft 070-483 dumps exam questions answers are updated (242 Q&As) and are verified by experts. The associated certifications of 070-483 dumps are MCP and MCSA.
Our exam questions have been authorized by the manufacturers and third parties. And has a large number of IT industry professionals and technology experts, based on customer demand, according to the outline developed a range of https://www.pass4itsure.com/70-483.html dumps to meet customer needs.